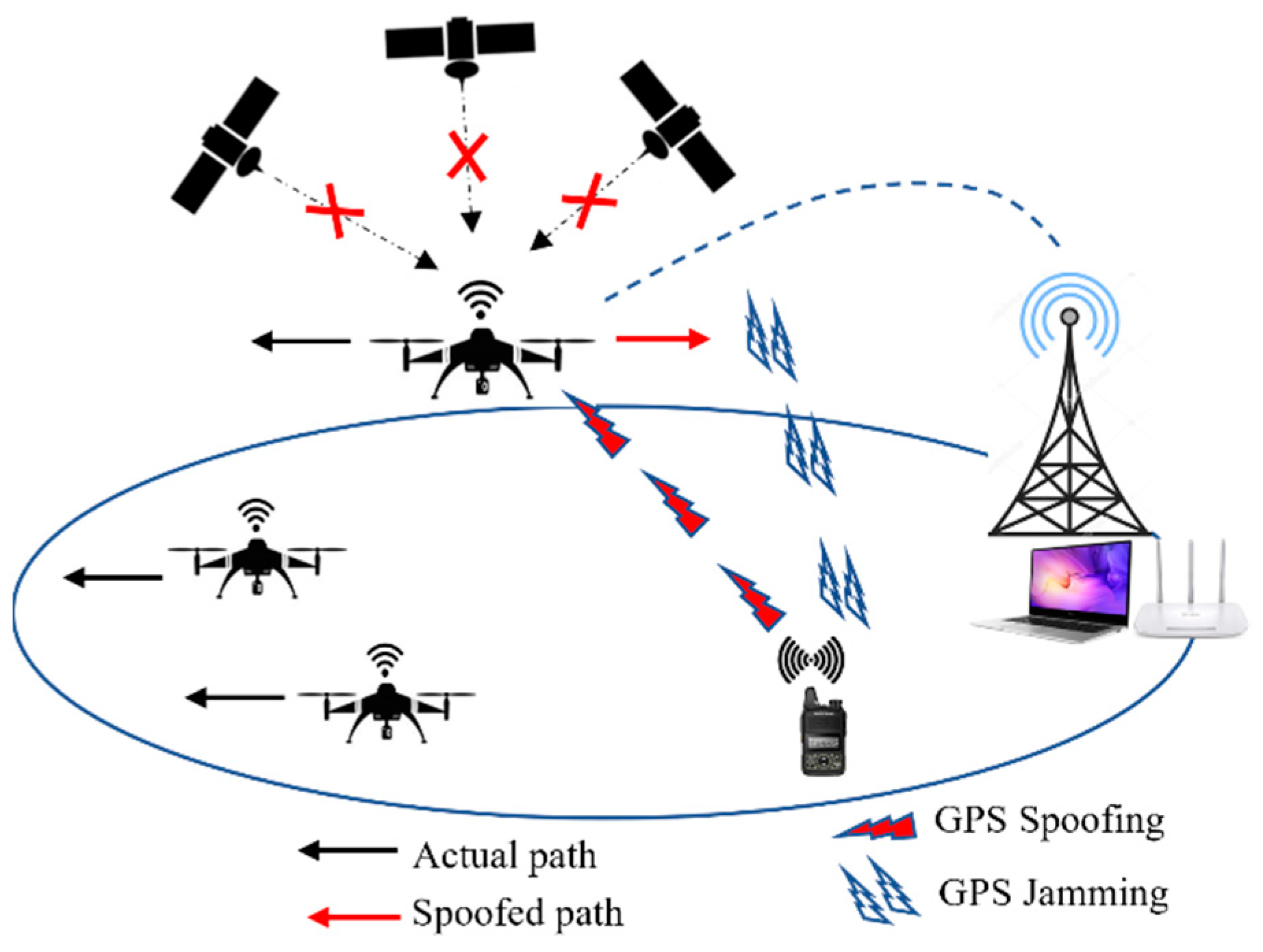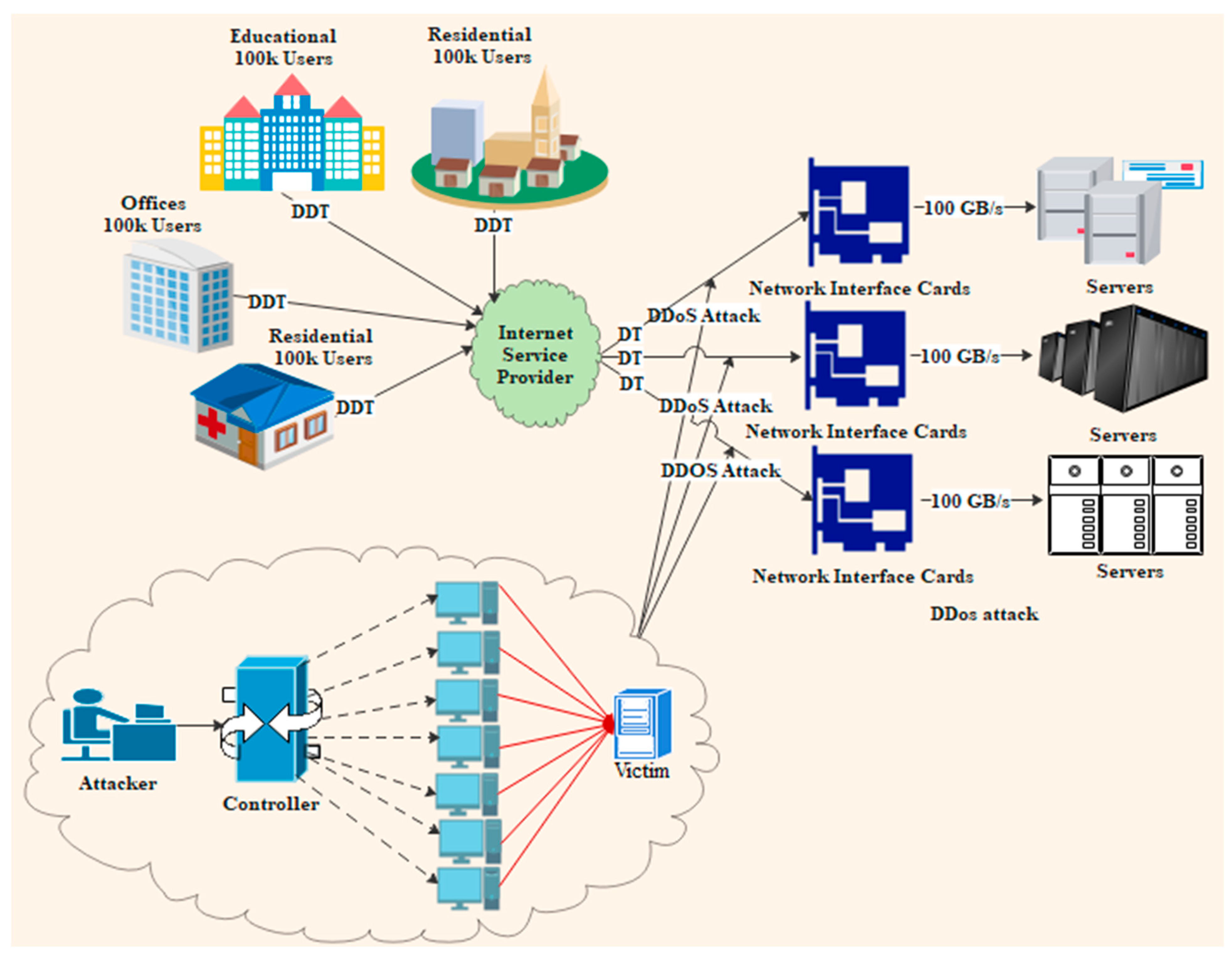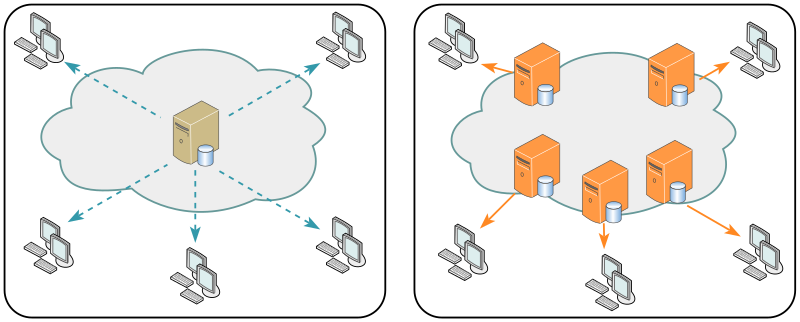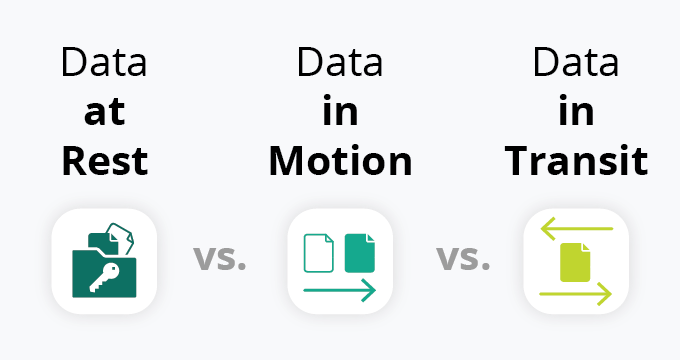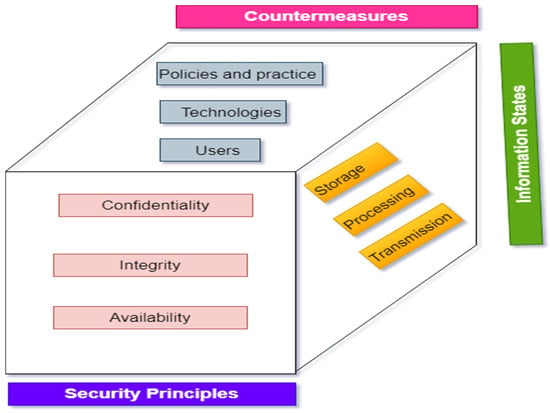
Electronics | Free Full-Text | A Comprehensive Review of Cyber Security Vulnerabilities, Threats, Attacks, and Solutions

Softswitch : Architecture for VoIP (Professional Telecom): Ohrtman, Frank: 9780071409773: Amazon.com: Books
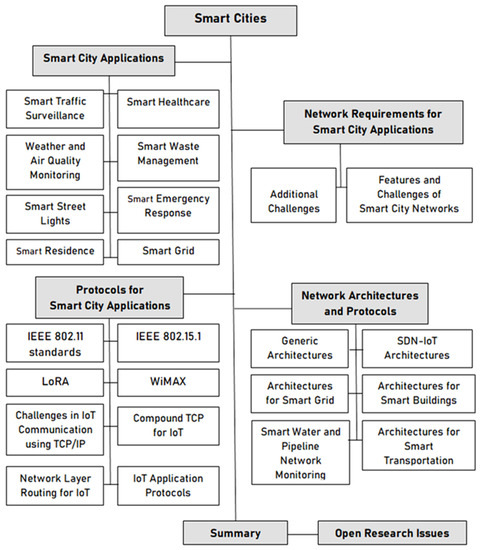
Electronics | Free Full-Text | Networking Architectures and Protocols for IoT Applications in Smart Cities: Recent Developments and Perspectives

New iOS 16 Exploit Enables Cellular Access Under Fake Airplane Mode , Cuba Ransomware Uses Veeam Exploit Against U.S. Organizations, and TP-Link Smart